Interest needs to be paid to making sure that the business's staff members understand as well as follow cybersecurity concepts, and will certainly not (un) intentionally compromise the corporate network security with their activities. Nonetheless, cybersecurity procedures used inside the company might differ depending on the firm's size, its monetary abilities, the market it operates in (managed or non-regulated), the info it has to take care of throughout business activities, and so on.
Depending on their intricacy, these degrees can be established with the help of a business's IT department or a cybersecurity services carrier. best rated Dallas IT servicesThe bottom line of Level 1 cybersecurity is to ensure the defense of the company network from the, e. g., phishing assaults (web links to destructive sites or downloads infected with infections are affixed to e-mails or instantaneous messages and sent out to a firm's staff members) and also malware (harmful software reaching a company's network using web or e-mail and existing in the form of spyware, ransomware, browser hijackers, etc.).
Network Security Threats: Ways To Protect Yourself
Tiny as well as not widely-known (a minimum of not yet) companies that do not manage information important for cyberpunks (e. g., client personal data like credit score card numbers, passwords, and so on) may barely become targets of advanced cyberattacks like DDoS (Distributed Rejection of Solution) or spear phishing. The minimum of cybersecurity actions necessary for the implementation is an effectively collaborating.
Antiviruses make sure security from such cyberthreats as ransomware, worms, spyware, and so on by checking each file the workers open or download and install from the web or other sources. To use these safety procedures, there's no demand in arranging a separate cybersecurity department. A company's can take obligation for this, as applying firewall defense, mounting anti-viruses software as well as continually maintaining their efficiency does not require cybersecurity-related abilities.
Carrying out vulnerability analysis and infiltration screening suffices for a tiny organization performing their business in a non-regulated market. These cybersecurity solutions performed on a yearly basis won't lead to heavy costs for a firm with a minimal budget plan. At the exact same time, these tasks can aid system managers to remain familiar with taking place protection weaknesses inside the company's network.
How To Keep Your Company's Network Secure
In this instance, assaulters' objective is to swipe any useful info from any kind of IP address susceptible to recognized safety weaknesses potentially existing in the corporate network. The chance that will certainly fall victim to non-targeted strikes is excellent.
Therefore, they may be easy to endanger. To make certain advanced protection of the business network, in addition to the components of very little security firewalls and anti-viruses the list below parts should be applied: indicating a variety of techniques (scanning emails for malware, filtering spam, etc.) to keep business details protected both in the 'inner' as well as 'outside' email communication from any cyberattack utilizing email as an entry factor (spyware, adware, etc.).
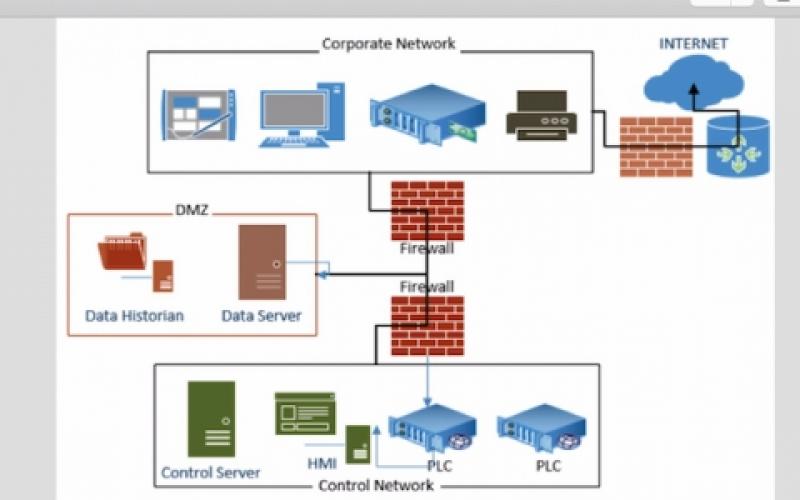
What's more, network segmentation implies separating the network properties storing a company's information from the outside-facing segments (internet servers, proxy servers), hence decreasing the threat of data loss.
Network Security Issues: Tips To Keep Your Business Secure
To maintain this level of network safety, a business requires info safety experts in charge of identifying and also managing cybersecurity risks, establishing safety treatments and policies, etc. For these objectives, the company might arrange their own or resort to a (MSSP). Organizing a different details safety and security division suggests heavy expenditures both on hiring a knowledgeable safety group as well as getting the required tools and also software program.
Nevertheless, the company will certainly still require an in-house safety policeman to collaborate the deal with MSSP. To control the performance of cybersecurity security, a thoroughly made need to attend to susceptability analysis as well as infiltration testing to identify, minimize and also handle cybersecurity threats. A firm requires a cybersecurity approach as it concentrates on shielding the corporate network thinking about the personnel utilizing their individual mobile tools and also laptops for business objectives (BYOD), wide usage of cloud computer, etc.
The key job of Degree 3 cybersecurity is to make certain the protection of the corporate network from targeted strikes. This sort of cyberattacks (spear phishing, the spread of innovative malware, etc.) suggests particularly established projects conducted versus a certain company.
The Death Of The Corporate Network
Firms running in managed fields should pay miraculous attention to keeping defense from cyberthreats while remaining compliant with policies and also standards (HIPAA, PCI DSS, and so on). The complying with cybersecurity parts might help to close all possible attack vectors: One security method implies securing gain access to by each gadget (a smartphone, a laptop computer, etc.) getting to the company network and also therefore ending up being a possible access factor for safety and security hazards.
The mix of these steps allows to check the activities customers execute when accessing the business network remotely from their smart devices, tablet computers, and also various other tools. As a result, the firm gets far better real-time presence over the whole variety of prospective safety hazards they may have to handle. Applying this step is exceptionally important within an enterprise involved in the financial or healthcare field.
DLP may reject the efforts to ahead any type of organization email outside the corporate domain name, upload company files to open-source cloud storage spaces, and so on.